This is MK from NTT Com DD Innovation CoE team. Recently I have successfully achieved the (ISC)²
CISSP certification and it was a fruitful journal along the learning path which really helps to improve
my security knowledge and understanding of security principles. I’m sincerely appreciate for the
encouragement from our organization that provided to employees for continuously learning.
I’m glad to have this opportunity to do a sharing for some security knowledge,
in here I would like to share an information security model namely CIA Triad.
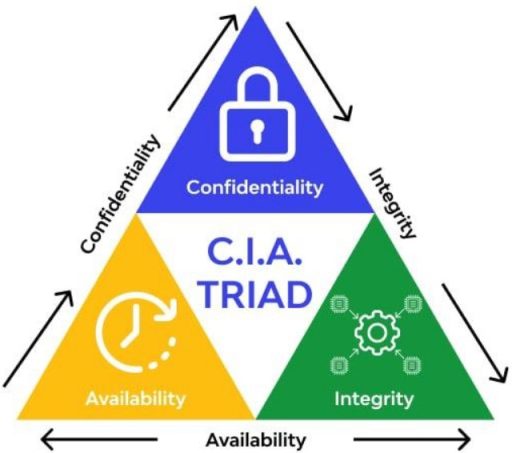
What is CIA Triad?
CIA Triad is covered under CISSP domain 1“Security and Risk Management” and it’s the three critical
security concepts: Confidentiality, Integrity, and Availability. Together, these three principles form
the pillars of information security known as the CIA Triad, an information security model meant to
guide an organization’s security procedures and policies. Typically viewed as primary goals and
objections to successfully design and deliver for the security infrastructure.
Ideally, when all these principles have been met, the organization possess a stronger security profile
against the security threats, vulnerabilities, and risks.
Confidentiality
The first principle of CIA Triad is confidentiality. Confidentiality is the concept of protecting to
maintain the secrecy of data, objects and resources and limiting the access to authorized users and
systems while restricting the access from unauthorized parties. The objective is to prevent the data
and information leakage which possible runs the risk of contractual and regulatory obligation for
data protection, and commonly reputation damage for the companies with known data breaches.
The countermeasures to protect confidentiality:
Encryption – Perform appropriate encryption at rest to encrypt data on storage and encryption in
transit to encrypt data while transmitting across the links and devices.
Data loss prevention – Prevent the importance data and information disclose by authorized users
intentionally or unintentionally.
Strict access control – Apply strict access on physical controls, logical/technical controls,
and administrative controls.
Rigorous authentication procedures – Implement multifactor authentication with at less two
authentication types such as password (Type 1) and token (Type 2).
Data classification – Classifying and labeling the data and assets based on value to the
organization and apply the appropriate protections and handling accordingly.
Integrity
The second principle of the CIA Triad is integrity. Integrity is the concept to maintain the authentic,
accuracy, and completeness of data. Integrity protection prevents unauthorized alteration of data,
with the proper integrity protection provides a means for authorized changes while against
the unauthorized activities such as malicious and viruses as well as the human mistakes
by the authorized users unintentionally due to accidents and oversights.
The countermeasures to protect integrity:
Strict access control – Assign least privilege to authorized users, only provide enough access to do
their job, no more and no less.
Rigorous authentication procedures – Implement multifactor authentication with at less two
authentication types such as password (Type 1) and token (Type 2).
Intrusion detection/prevention systems – To prevent and block intrusion
entering the networks and systems.
Hash verifications – To ensure the data integrity from alteration.
Interface restrictions – Interface restrictions on applications based on the granted access privilege.
Availability
The third and final principle of the CIA Triad is availability. Availability is the concept focused to
ensuring that authorized users can access data when they need it with reasonable amount of time so
it’s importance to ensure the systems, networks, and applications are functioning as expected.
Generally, the availability of systems and networks could be maintained with the proper design and
implementation that possibly cause by device failure, software errors, link disruption, etc.
The countermeasures to protect availability:
High availability – Implement high availability and redundancy for critical systems and networks
eliminating single point of failure.
Monitoring systems – Continuously monitoring links, systems performance, and networks traffic to
avoid overwhelming and overutilizing
BCP/DRP – To ensure the restoration of business operations in timely manner for any unforeseen
circumstances.
Backup systems – Perform schedule data backup and regularly perform verification for data restoration.
Systems and networks protection – Implement firewall, IDS/IPS, WAP, UPS, etc.
How can NTT Com DD Help?
Security always the priority for an organization and shouldn’t treat as afterthought.
As a solutions provider, we are emphasizing “Secure by Design” building security into solutions
from the very beginning practically during the design and architecture phase.
Our organization do provide a complete cybersecurity lifecycle for security consulting services,
technical services, support services, and managed security services.
With our strengths in cybersecurity, here are some parts of our solutions offering that enhance
confidentiality, integrity, and availability:
Zero Trust – Provides a comprehensive security approach securing all access across the networks,
applications, and environment from any user, device, and location.
Network security orchestration – Centralized security management layer allowing organizations
to define and implement a comprehensive security policy and perform policies optimization with
highly customizable workflow.
SASE – Cloud-based security components such as SWG, CASB, ZTNA, FWaaS, and RBI providing the
network security services over the WAN to securely connect users and endpoints to applications
and services anywhere from the globe.





