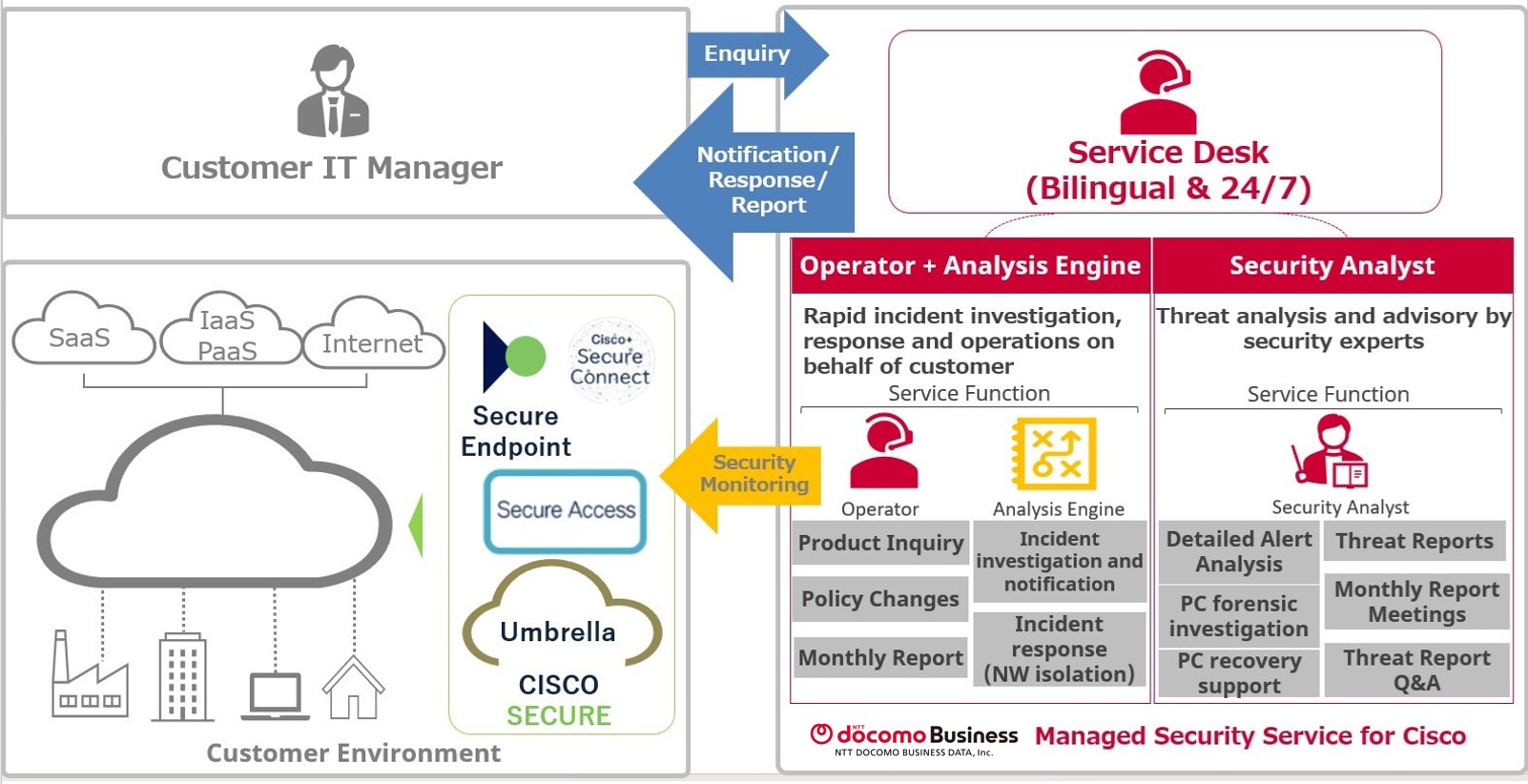
including security monitoring and incident response by the SOC (Security
Operation Center) as well as threat analysis by security analysts, utilizing
“Cisco Security Products※”.
※Support products: Cisco Secure Access/Cisco Secure Connect/
Cisco Secure Endpoint/Cisco Umbrella
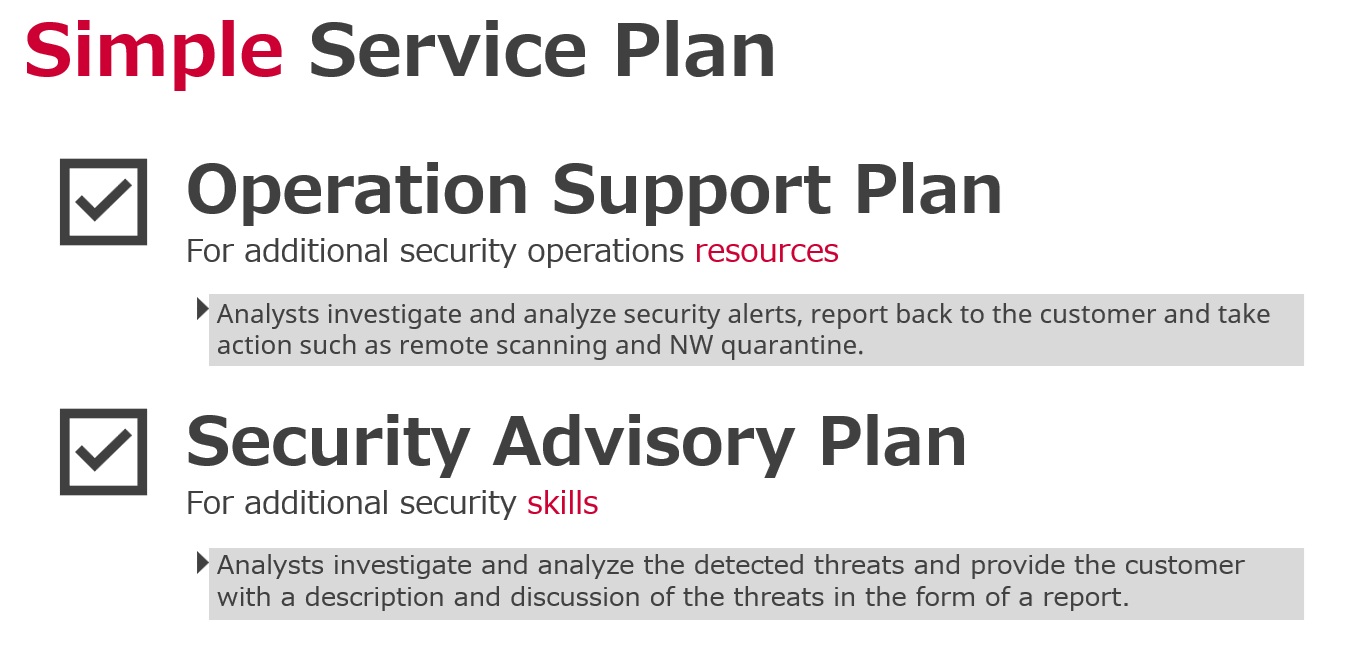
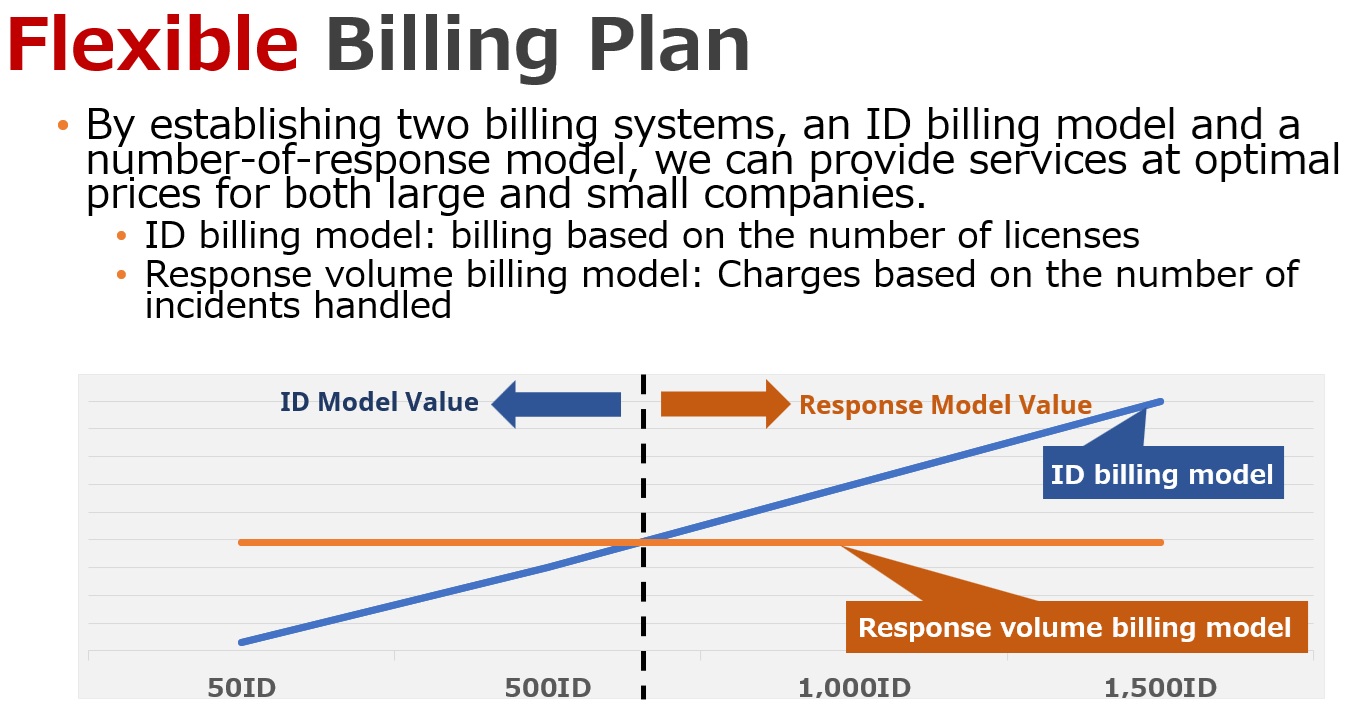

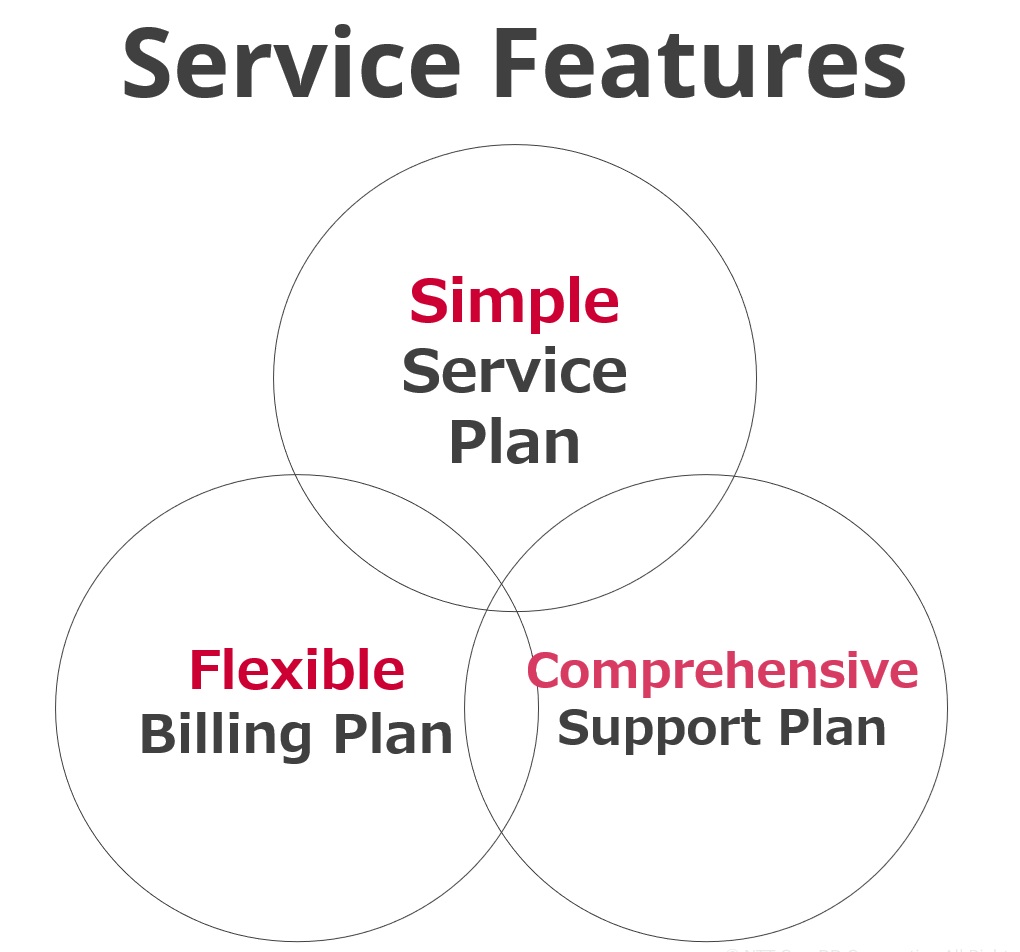
Effects of the Service Installation
~ Scope of the service for the expected process ~
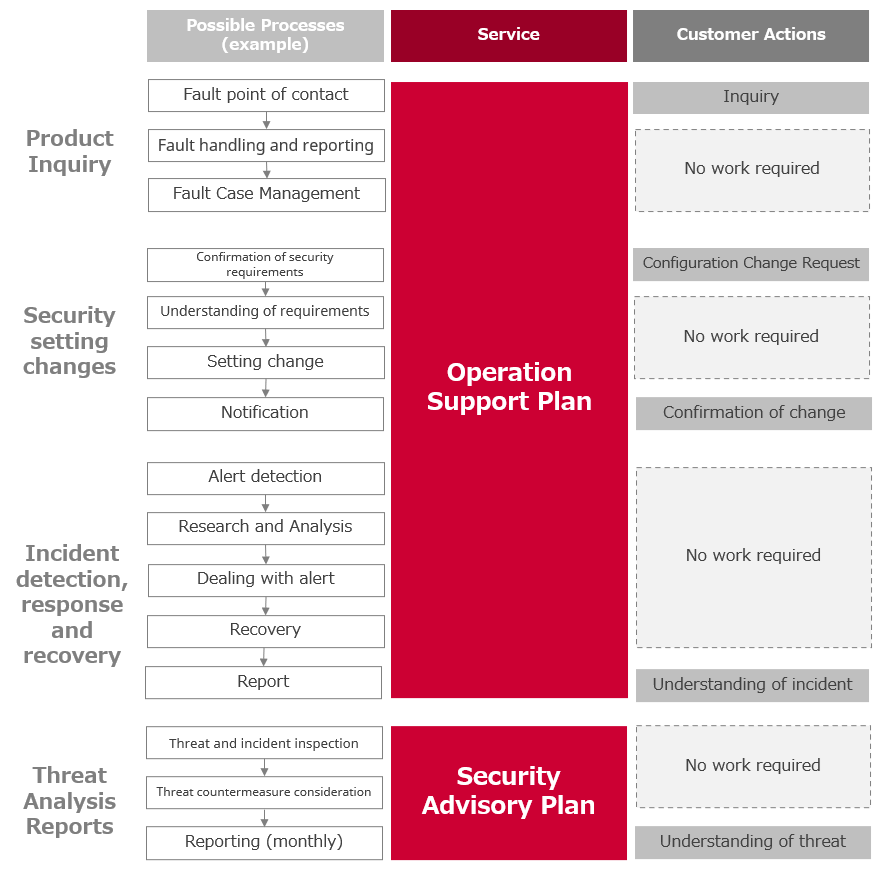
Functions | Description |
| Secure Endpoint | |
Product Inquiries | Responding to product failures and escalating to technical support team |
Incident Notification | Responding to security alerts and notifying content according to the threat level e.g. Quarantining the device if there is critical incident |
Incident Response | Responding to incidents according to the severity of the threat e.g., performing a flash scan, notifying scan results, and releasing quarantined devices |
Analyze Support *Optional | Investigating EDR logs in detail to provide findings and recommended actions |
Forensic Support *Optional | Analyzing evidence from the device related to the incident and reporting forensic results |
Recovery Support *Optional | Based on the forensic results, restoring data from backup for recovery work on the |
Change Policy Configuration | Based on the customer requests, Changing policy configurations e.g. white/blacklisting, policy changes |
Statistical Reports | Providing statistical reports for various responses |
| Secure Access/Secure Connect/Umbrella | |
Product Inquiries | Responding to product failures and escalating to technical support team |
Daily & Weekly Alert Notifications | Monitoring and notifying of high-risk traffic from Umbrella reports daily and weekly |
Real-time Notifications | Real-time notifications of suspicious traffic on specific devices |
Incident Response ※ | Responding to incident according to the severity of the threat e.g., performing a flash scan, notifying scan results, and releasing quarantined devices * Required the contract of operational Support Plan for Secure Endpoint. |
Whitelist Configuration | Responding to change configuration when blocked by Umbrella due to false positives * Required the approval from customer that confirm the risk level of the target URL |
Policy Configuration | Based on the customer requests, responding to change configuration e.g. white/blacklisting, policy changes |
Statistical Reports | Statistical reports for various responses |
| Functions | Description |
| Secure Endpoint | |
Threat Reporting | Analysis reports of threats detected in various products results based on each product * OSINT: Open Source Intelligence |
Report briefing session | Report briefing session (this line is repeated—consider removing the duplicate) |
Report Inquiry | Q&A support regarding the contents of the report following the briefing session |
| Secure Access/Secure Connect/Umbrella | |
Threat Reporting | Analysis reports of threats detected in various products results based on each product * OSINT: Open Source Intelligence |
Report briefing session | Report briefing session (this line is repeated—consider removing the duplicate) |
Report Inquiry | Q&A support regarding the contents of the report following the briefing session |