Hello, this is T.N. from the Product and Service Development Department.
In the Remote Work Security Series, which was published from December 2021 to June 2022, I have introduced an overview of the solutions. Since we understand that some customers may not be able to fully understand the solutions from just an overview, we would like to start this series with an introduction to how the solutions can be used in actual workplaces. In this first article, we will discuss the practical use of Cisco Duo. If you haven’t read the overview yet, please refer to the following link.
Remote Work Security Series – Part 3: Zero Trust with cloud-delivered Cisco Duo
https://nttcdd.jp/usecase/3312/
(*Currently in Japanese only. Will be updated when English version is ready!)
Contents
Security for Remote Connections to Azure
Convenience of Azure Cloud Services and the associated Security Risks
As readers may know, Azure is a cloud service provided by Microsoft, offering a convenient environment for users to adopt IaaS and PaaS. I had a chance to set up Azure as a beginner, and once I experienced it, I felt that I never wanted to go back to “on-premise” because of the conveniences it brings. (Of course, it is expected that customers with the most important data will continue to choose “on-premise”, so it will never completely disappear.) However, there are some security concerns with Azure. Therefore, in this blog, I would like to share mainly on the significance of using Cisco Remote Work Security (hereinafter referred to as Cisco SASE) as countermeasures to further enhance Azure’s security.
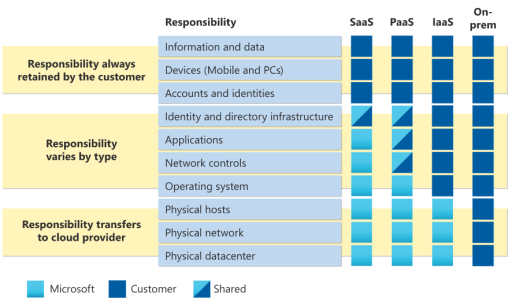
Are you familiar with Azure’s joint responsibility model?
Microsoft has a Shared Responsibility Model to address security aspects of Azure. In a simple explanation, it is a demarcation point between Azure customers and Microsoft Azure. For example, if you use IaaS, Azure is responsible for any security holes that allow an attacker to break into any virtual machine, but it is Azure customers’ responsibility if the attacker breaks in because of the configuration of a particular virtual machine. The configuration of the OS is also the responsibility of Azure customers. For example, on an On-Prem Windows environment, if the administrator has defined a policy to allow connections from any remote desktop and uses a simple username and password, then the administrator would be held responsible in the event of intrusion. Even after moving to the cloud, the customer will still be responsible for the security management of the workloads.
How and what can we do to further enhance Azure security?
So how should we take security measures on Azure? One way is to use the security tools provided by Azure. There are a number of free and paid security tools available, such as Azure Defender, Azure Firewall, and Azure DDos Protection etc.
However, it is important to note that cloud services are based on single sign-on (SSO) for authentication, and this would depend on the Azure configuration, if an attacker can penetrate the virtual machine running on Azure, the security tools would also be bypassed. When this happens, the risk increases.
Furthermore, upon a successful intrusion, a skilled attacker could use a rootkit to temper logs and perform other remote control activities without leaving any trace of intrusion, so it is not a good idea to store security-related logs on the same Azure server.
Based on these considerations, it’s recommended to implement additional security measures from a different vendor on top of the security features offered by Azure. Therefore, from the next chapter, we will examine and evaluate how to enhance Azure security by specifically linking Cisco ASAv to Duo, one of the components of Cisco’s SASE to further secure the workloads on Azure.
Validation Objective and Architecture Diagram
The following are the goals, products used, and configuration diagram used in this validation exercise.
- Objective: To evaluate the effectiveness of using Cisco SASE to enhance the security of remote work connections to Azure.
- Products used: Cisco’s ASAv and Duo
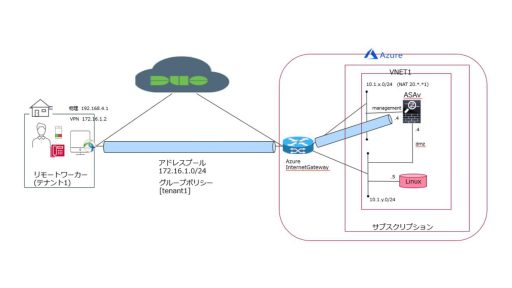
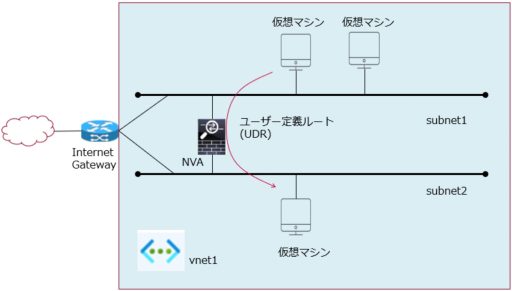
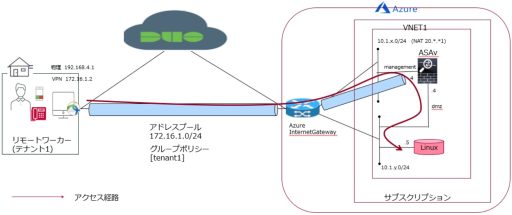
- Architecture diagram: The figure below depicts accessing a Linux instance hosted on Azure from a remote worker.
Preparation: environment of Azure
Some basics of Azure
Before I get into the main topic, I would like to describe a few basics of Azure to help you better understand the validation report in this blog. At a minimum, you will need to be familiar with Azure’s licensing structure, resources, and the concept of “VNet”. For more information on Azure, please refer to the Microsoft documentation on Azure.
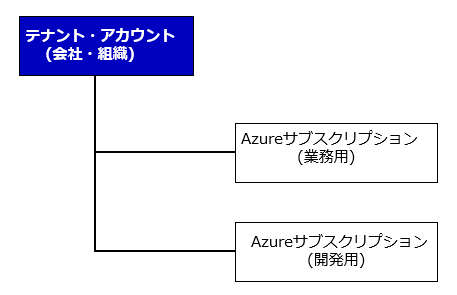
(1) Azure Licensing System
Azure licensing is based on a “tenant” (company or organization) at the top, with subscriptions under the “tenant”. For example, as shown in the figure below, an organization can have a contract for business use and a contract for development use.
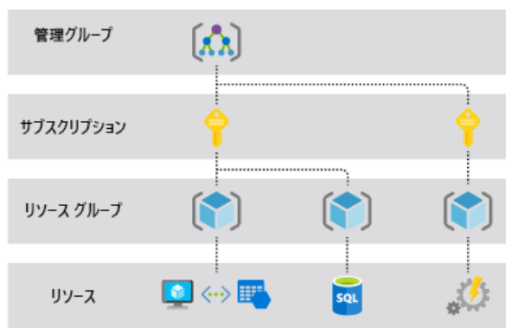
(2) Resources
Resources such as virtual machines and virtual networks are tied to subscriptions. Resources can be grouped, and common policies such as Azure’s simple security and alert settings can be applied to resource groups.
(3) VNet
The Azure network is divided into VNet units, and if multiple subnets are created in a single VNet, they can be routed through the Azure Gateway. It is important to note that access is allowed by default. If you want to control the access between subnets, you can use a firewall such as Cisco ASAv to create user-defined access policies. One significance of installing Cisco security products occurs here.
ASAv preparation
Now that you have some basic understanding of Azure, the next step is to implement Cisco ASAv in your Azure environment. Cisco ASAv is deployed from Azure’s Marketplace. Please refer to the instructions provided by Cisco below for more details.
<Prerequisites>
- Basic knowledge of ASAv is required.
- Please configure the initial settings of ASAv based on the link provided in the following procedure.
<Procedure>
Please refer to “Cisco Adaptive Security Virtual Appliance (ASAv) Getting Started Guide, 9.17” on Cisco’s support website.
<Points to note>
- Four ASAv interfaces are required.
- Shutdown is OK for unused interfaces.
- The management interface serves as both the ASAv management network and Internet communication (VPN communication).
※Costs for ASAv
ASAv license usage rights are contracted with Cisco, while CPU, memory, and other resource usage to run ASAv is contracted with Microsoft.
<Deployment steps>
Below are the steps of deploying ASAv from the marketplace.
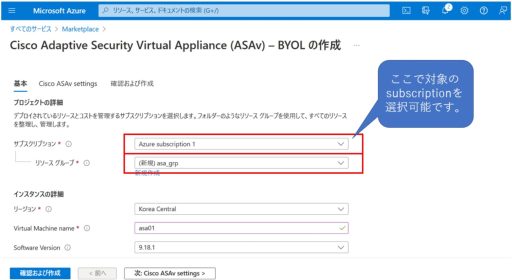
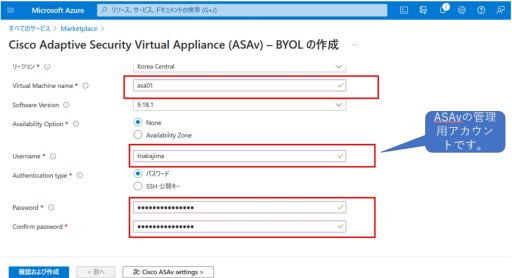
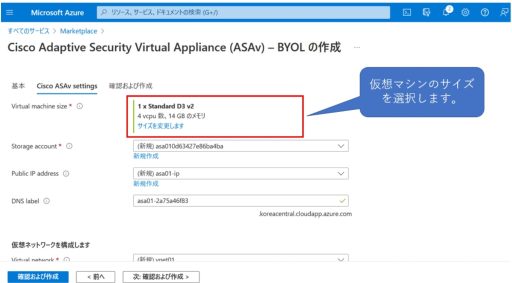
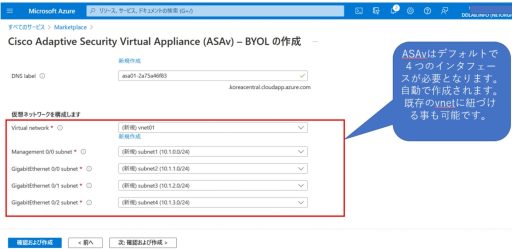
ASAv + Duo Configuration Settings
Chapter 3 describes the configurations of ASAv and Duo. The configuration steps can be found in the Cisco Duo related procedures below. In addition, we have included the workaround against “self-signed certificate errors” in the “Additional Information” section below.
Configuration of Remote Access VPN in ASAv
<Prerequisites>
- Basic knowledge of Remote Access VPN in ASAv.
- Basic knowledge of Duo is required.
<Procedure>
Please refer to “Duo Single Sign-On for Cisco ASA with AnyConnect” on Cisco DUO page and “CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.17” on Cisco’s support page.
<Points to note>
- Install Anyconnect version 4.10.* or later.
- Select ASA OS version 9.18.* or later. (For SAML authentication with External Browser)
- Establish a VPN on the Management interface.
- For Linux access, write routing in ASAv and configure a user-defined route in Azure.
<Deployment steps>
In the above procedure, ASAv is configured from the GUI (ASDM), and the deployment steps will show how the configuration looks like in the CLI.

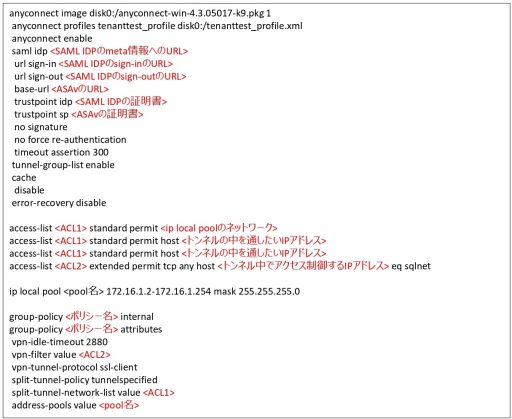

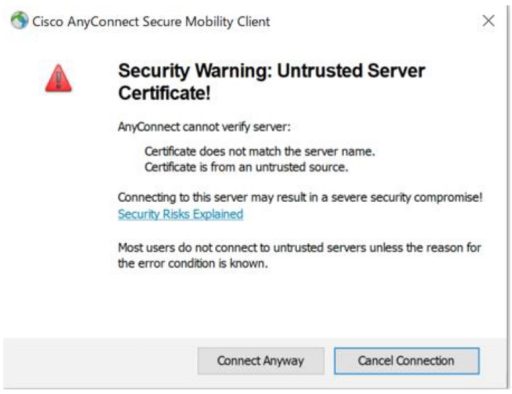
<Additional Information: Workaround against “self-signed certificate errors”>
When doing SAML authentication for remote access VPN with ASAv, AnyConnect uses the built-in browser by default. If the built-in browser uses a self-signed certificate, a security error will occur and access will not be possible.
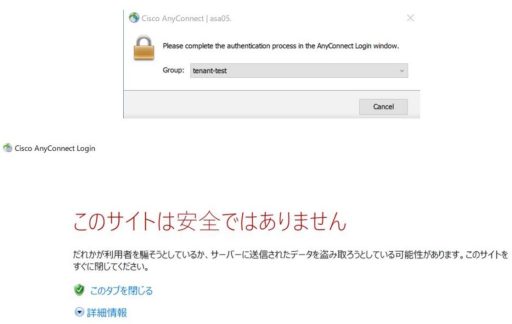
Therefore, you can configure AnyConnect to use an External Browser (e.g., Microsoft Edge) for SAML authentication during verification: download anyconnect external-browser-pkg from Cisco’s Software Center and then upload the software to ASAv. Then activate the External Browser from the CLI.

Duo configuration
Section 3.2 describes the Duo configuration for this verification.
<Prerequisites>
- DuoClient must be installed on the cell phone to be used as the MFA device.
- Basic settings for Duo must have been completed.
<Procedure>
Please refer to “Duo Single Sign-On for Cisco ASA with AnyConnect” on Cisco DUO’s page.
<Points to note>
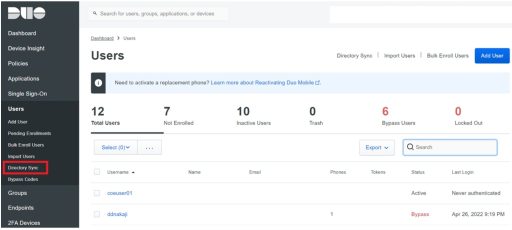
- Synchronize users with Azure AD and Duo’s Directory Sync.
- Enable SSO.
- Enable ASA Remote Access VPN in the application.
<Deployment Steps>
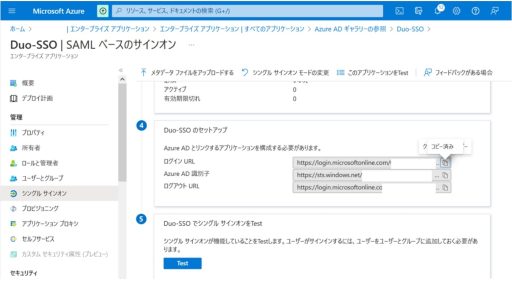
(1) Azure
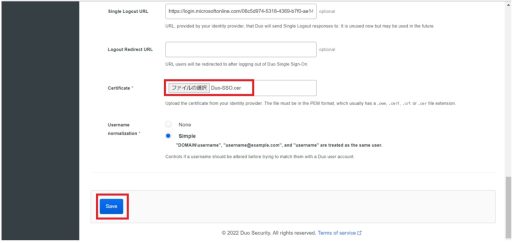
Below are the settings that need to be configured on Azure:
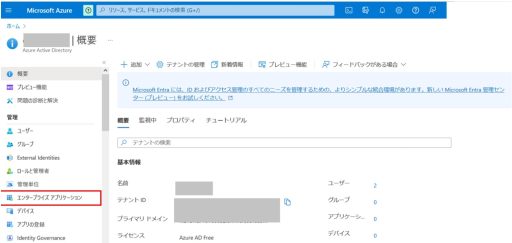
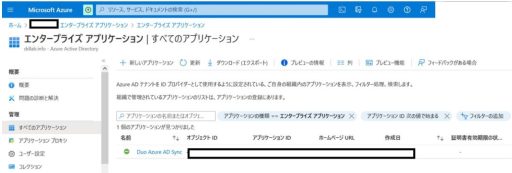
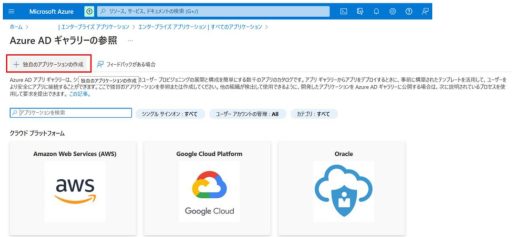
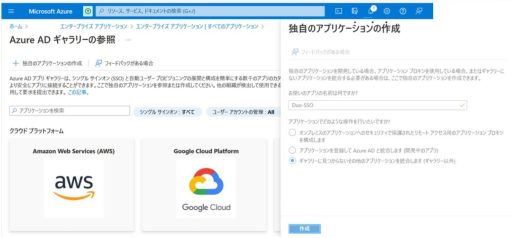
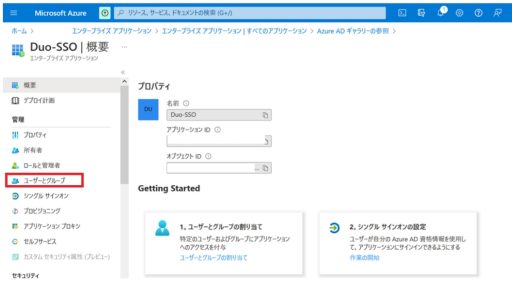
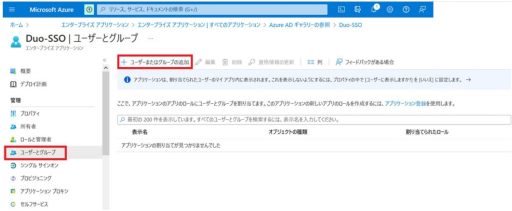
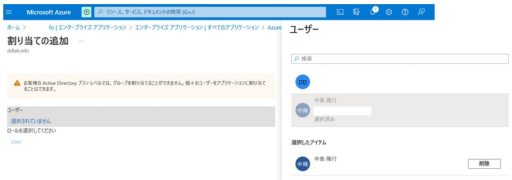
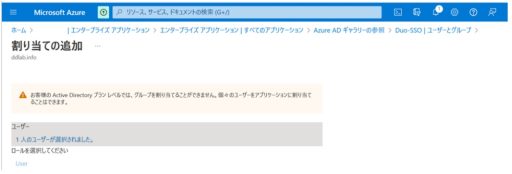
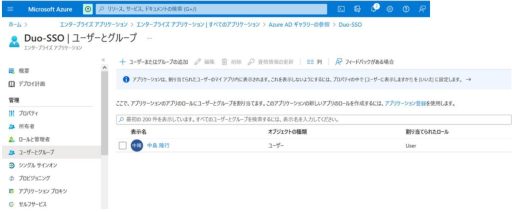
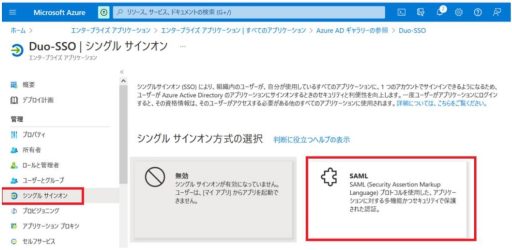
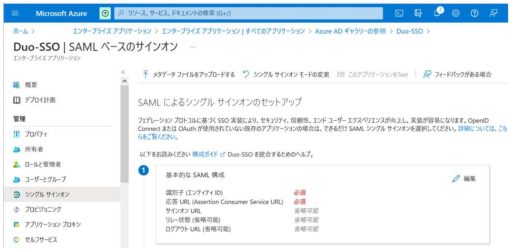
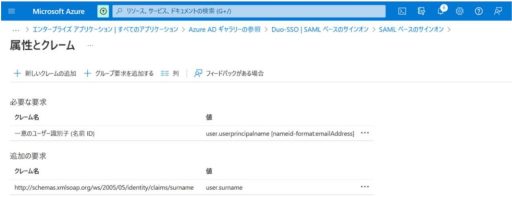
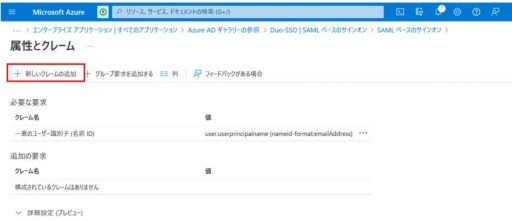
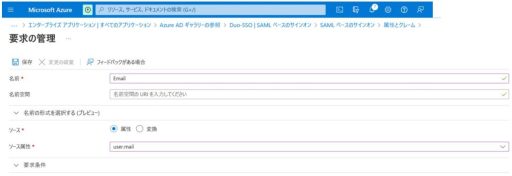
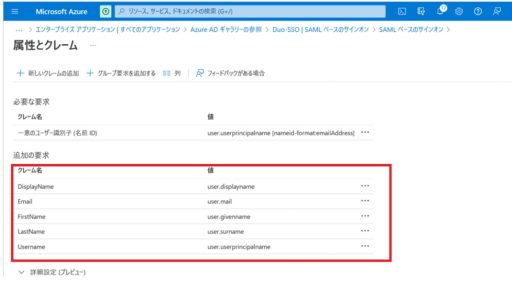
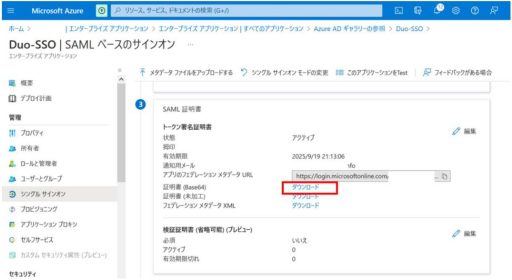
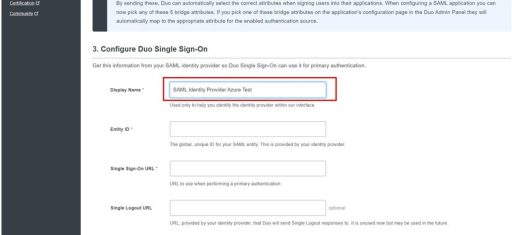
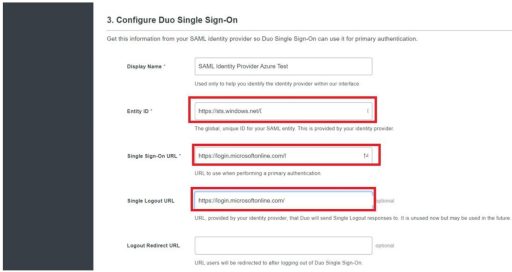
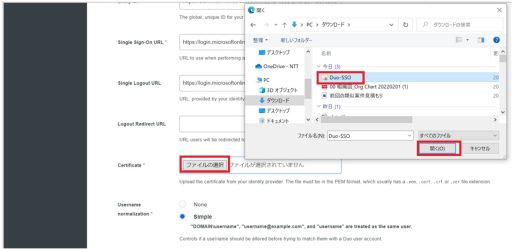
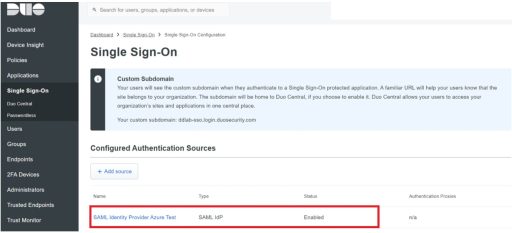
(2) Duo
Next, you need to set up Duo. Below are the settings that need to be configured on Duo:
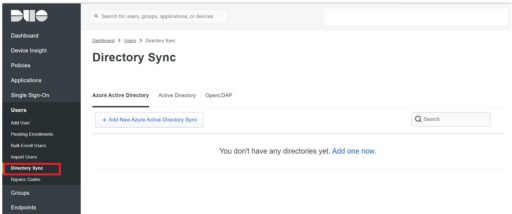
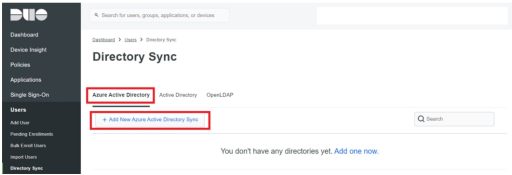
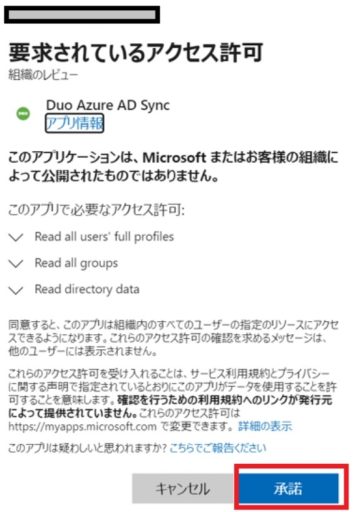
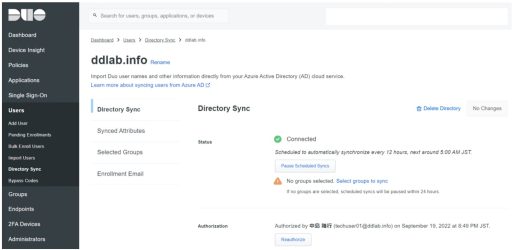
Test Results
Access Verification
In section 4.1, we describe the results of establishing a Remote Access VPN between the remote worker’s endpoint and ASAv on Azure, and verifying to the point of pinging the Linux instance on Azure.
<Points for confirmation>
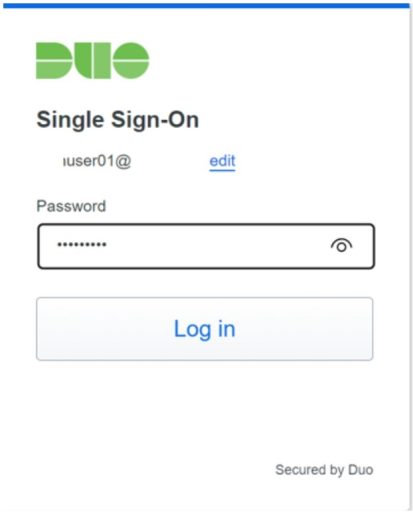
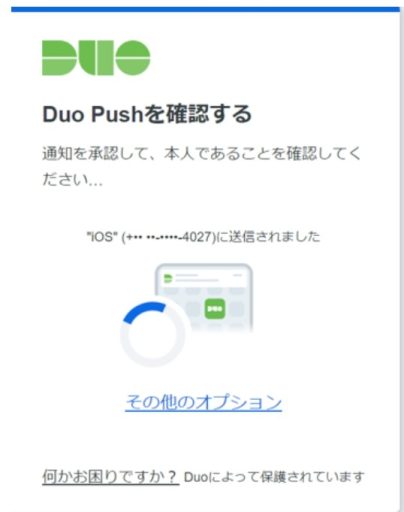
- The VPN authentication is based on SAML authentication, so that the identity of the user is thoroughly verified by Duo’s multi-factor authentication.
- After the VPN is established, remote workers can directly access the Linux instance on Azure.
- Security logs are managed by Duo Cloud.
<Verification Steps>
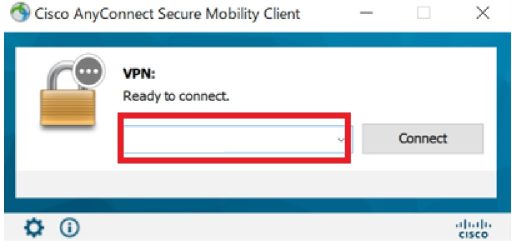
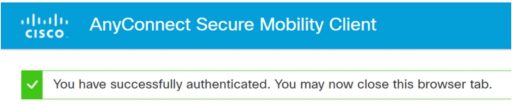
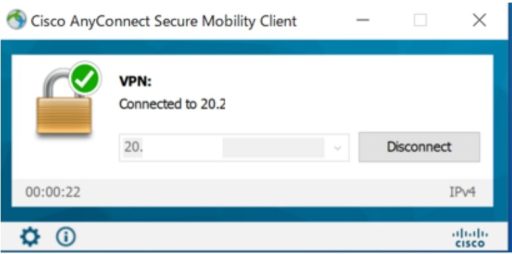
(1) Establish VPN with AnyConnect
Launch Cisco AnyConnect Secure Mobility Client from the task tray, enter the IP address or FQDN of the ASAv to be accessed, and click the Connect button.
(2) Result of Ipconfig
Confirm that the IP address is assigned from ASAv as shown in red.

(3) Result of Ping check
Confirm that ping communication is established with the Linux Instance on Azure.

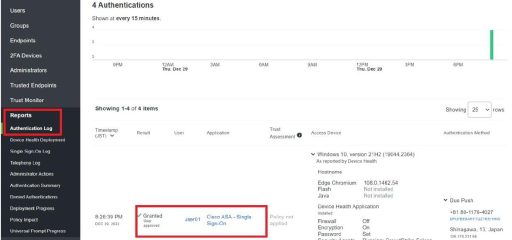
Results of checking Authentication Log on Duo
In section 4.2, we check the authentication log on Cisco Duo. The figure below shows that SAML authentication was successful when establishing a remote access VPN with ASAv. Note that this is managed in the Cisco cloud, which is separate from the Azure environment, so it cannot be tampered with by a rootkit or other attack. This is the second advantage of using Cisco SASE.
Evaluation of Verification Results
- Finally, we would like to summarize our evaluation of the validation results as objectively as possible as follows.
- Cisco ASAv enables us to use remote access VPN.
- Cisco ASAv enables flexible access control and routing within Azure Vnet.
- By integrating Cisco Duo and Cisco ASAv, the remote access VPN between ASAv and remote workers can be authenticated with SAML authentication to ensure identity verification. (Realization of zero-trust level security)
- Authentication logs are separate from Azure, so there is no need to worry about them being tampered with by an attacker.
Summary of this blog and notice of next issue
In this blog, we discussed how Cisco SASE (ASAv+Duo) is used to enhance security measures for remote access to Azure. If you have any questions, please feel free to contact us. In the next issue, we will report on how remote access using the Cisco Umbrella roaming client can be used in the real world. Please stay tuned for our next issue.
Please click the blue button below to contact us!

![[Remote Work Security Practice: vol.1] Enhancing security of remote work connections to Azure with Cisco ASAv and Duoのイメージ](https://nttcdd.jp/en/wp-content/uploads/sites/2/2023/08/azure-1024x576.jpg)



